Kidnapping Case Study
The Influencer and the Kidnappers
How Digital Shadows Led Us to the Truth
Brief
A Lagos social media influencer disappeared. No witnesses. No direct evidence. Only a trail of social media posts.
I’m an anti-kidnapping investigator. This one was mine to solve. With my team, we combined OSINT and Ad Intelligence to map his digital footprint, trace his captors, and locate the site where he was held. Every detail mattered. In cases like this, time is the difference between rescue and loss.
Kidnappers often discard or switch off victims’ phones, making traditional tracking methods unreliable — so we must rely on alternative digital intelligence to find them.
Step 1 — Analyse the Victim’s Call Detail Record
The victim disappeared around 6 p.m. A few hours later his fiancée received a ransom call. My first move was to verify the number that made that call. I used Discovery, to check if the number was active and traceable. The result was clear: the number was a burner, with nothing connected to it, and it was already offline. That meant there was no way to track the kidnappers directly through it. I set a logon anyway so I’d know whenever the device was turned on.
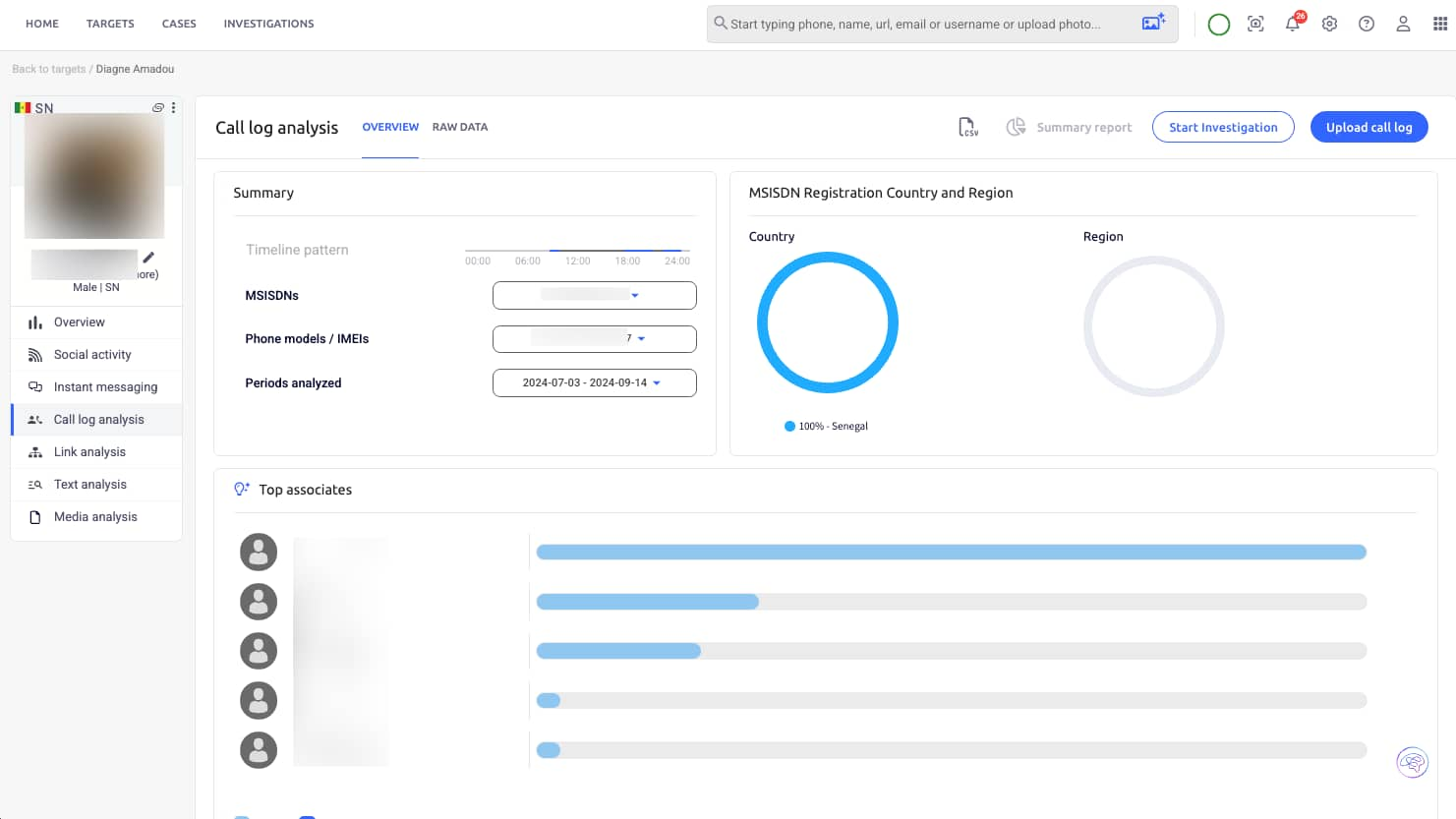
I then turned to Azimuth, a telco data AI system, which helped me analyse the Call Detail Records of the victim. Doing so, I could establish who the victim had been speaking to, when, how often, and where those trails might lead. This gave me the first layer of context around his disappearance and the baseline for building his broader digital footprint.
We followed up. A friend confirmed they watched a film that night. With that, Melissa’s alibi held. We couldn’t do more. Not without a reason. But the number in the victim’s pocket still led back to her. And it stayed with me.
Step 2 — Build a digital profile with OSINT
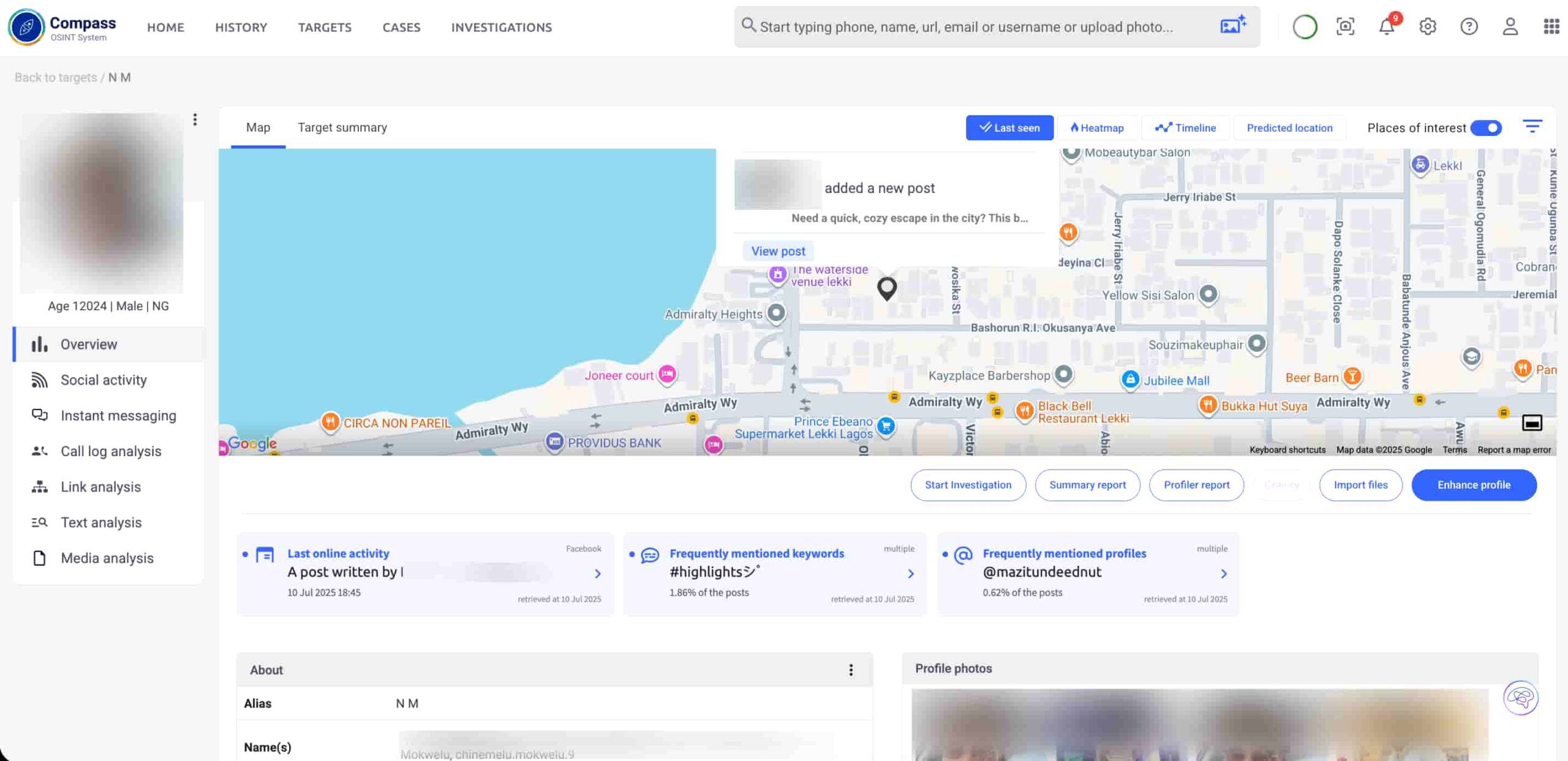
The victim, known online as a rising influencer, showcased luxury rentals and gym sessions on Instagram. He frequently tagged a popular fitness gym and highlighted new client deals.
Using Compass, an OSINT system, I built his digital footprint profile. His posts revealed the gym, his managed properties, an upscale restaurant, and his residence. Those became our first investigation points.
Step 3 — Confirm the Surveillance with ADINT
The kidnappers knew his routine, so I needed to know how. My next step was to confirm if anyone was following him.
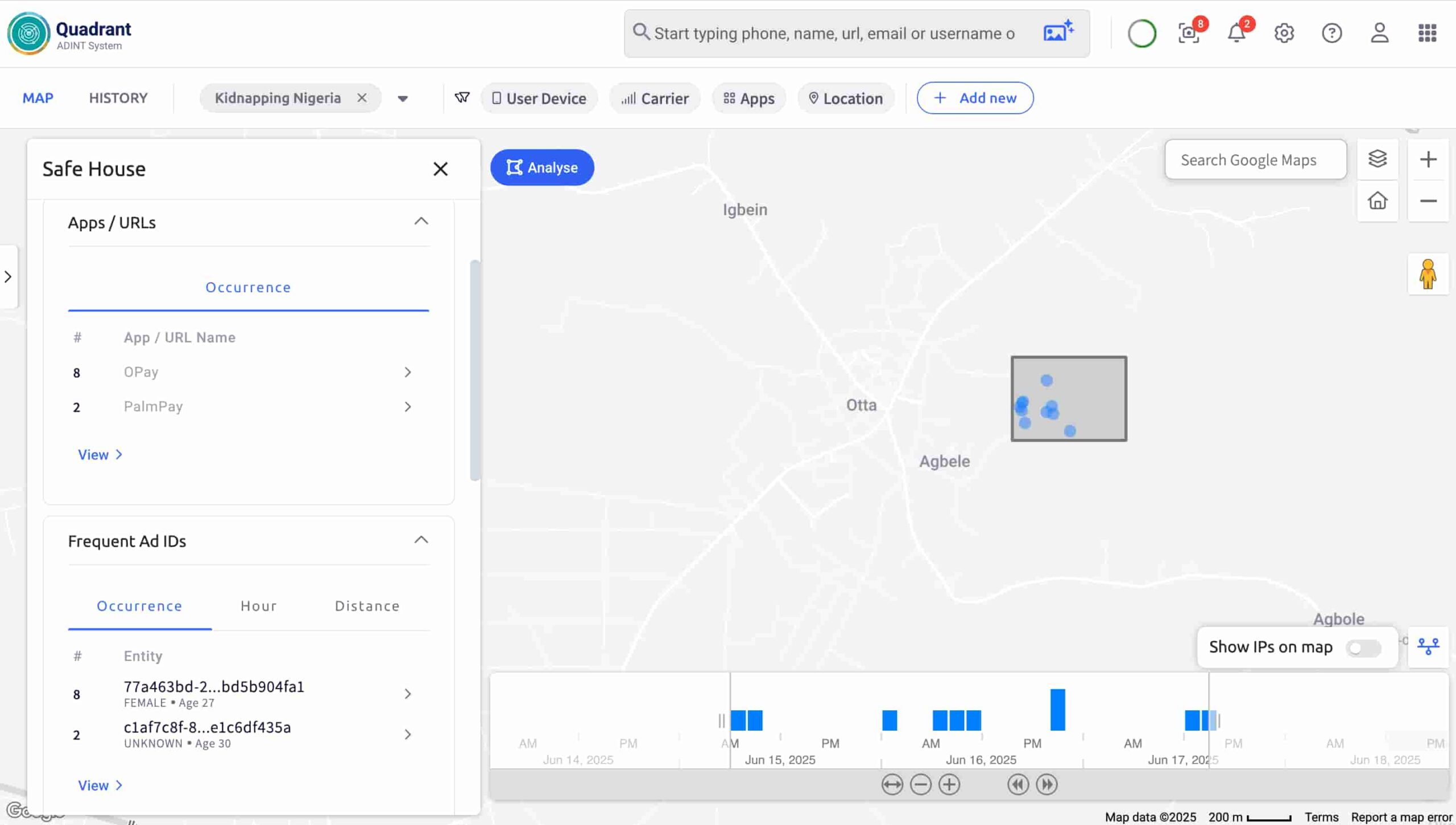
I used Quadrant to collect Ad-IDs in the vicinity of the gym he frequented. Quadrant uses ad data from smartphones present in an area of interest.
I defined the gym’s location and a timeframe from his recent posts and pulled the Ad-IDs of all the devices present during his visits. Quadrant automatically cross-referenced their movement patterns and highlighted two frequent devices that appeared alongside the victim. These devices, we suspected, belong to the kidnappers.
This confirmed our suspicion: the victim had been under surveillance.
Step 4 — Trace the Victim’s Movement
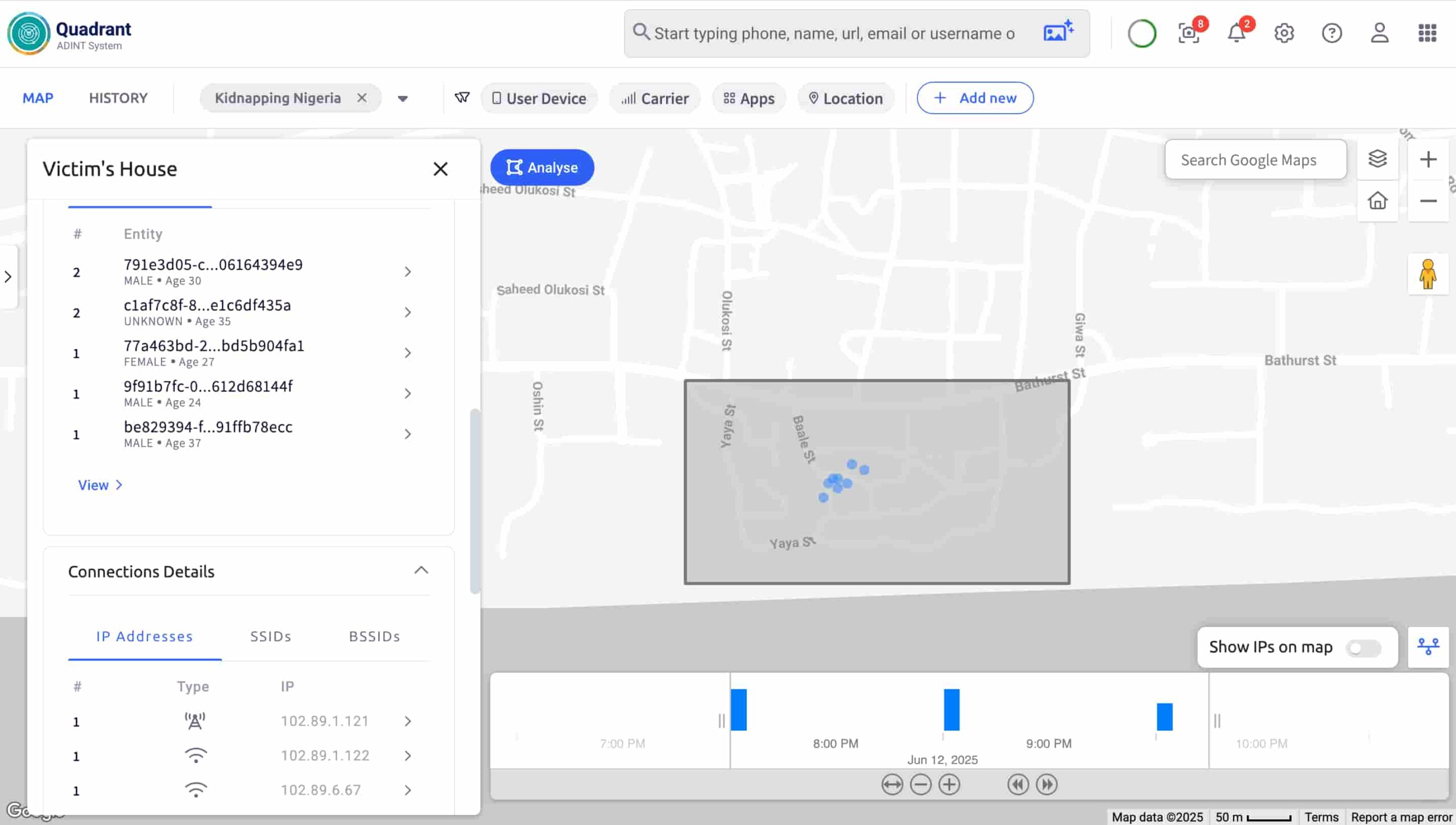
With the surveillance confirmed, I used Quadrant to trace the victim’s movements leading up to the abduction. It helped me map his routine across the gym, the two rental houses, the upscale restaurant, and his home.
At each location, the same two suspect devices reappeared. This correlation validated that we were tracking the right person and provided a detailed timeline of the victim’s routine.
With that timeline and the victim’s routine mapped out, we could plan our next steps.
Step 5 — Pinpoint the Criminals’ Base
I now had two Ad-IDs that I was more than sure belonged to the kidnappers. To find their base of operations, I ran a historical movement analysis on both devices. I was looking for a pattern, a place where they frequently met or paused for extended periods.
Both devices were repeatedly active at the same time in a remote, unpopulated area. This was their meeting point, a likely safe house or planning site. That insight gave us a location to focus on, narrowing down the search significantly.
Tactical teams were mobilised through official channels to target the suspected safe house.

Outcome
By correlating OSINT with ADINT, we followed the digital trail from public posts to hidden devices, from surveillance patterns to a remote safe house. What began as a disappearance ended with a life saved and a family reunited. Beyond the data and devices, every case like this reminds us of the real human cost of kidnapping and the urgency of bringing people home safely.
This is what Securing Better Lives looks like.
Book a demo
Experience how Intellectus helps agencies solve cases faster, with a live demo from our team.

