Terror Attack Case Study
Preventing Cross-Border Terror Attacks
From digital traces to decisive action using behavioural intelligence.
Brief
It’s 3:00 am. An intelligence officer reviews new intel received overnight. Three phone numbers. No names. No backstory. Just a HUMINT report with a warning: people behind those numbers are tied to a group planning an attack near the northern gendarmerie post in Koundjoaré.
This use case shows how a single starting point can turn into a network. How advanced AI helps prevent violence before it begins. How every trace matters. This is how we Secure Better Lives.

Step 1 — Confirm the presence
I ran the numbers through Compass. Compass is TRG’s open-source intelligence tool that checks for public online activity like messaging apps, social media profiles, or linked usernames. None of them were linked to any public social media or messaging accounts. We had no names, no photos, no clear user activity.
But if the numbers were real, they’d be active.
If they were active, we would see them in Discovery.
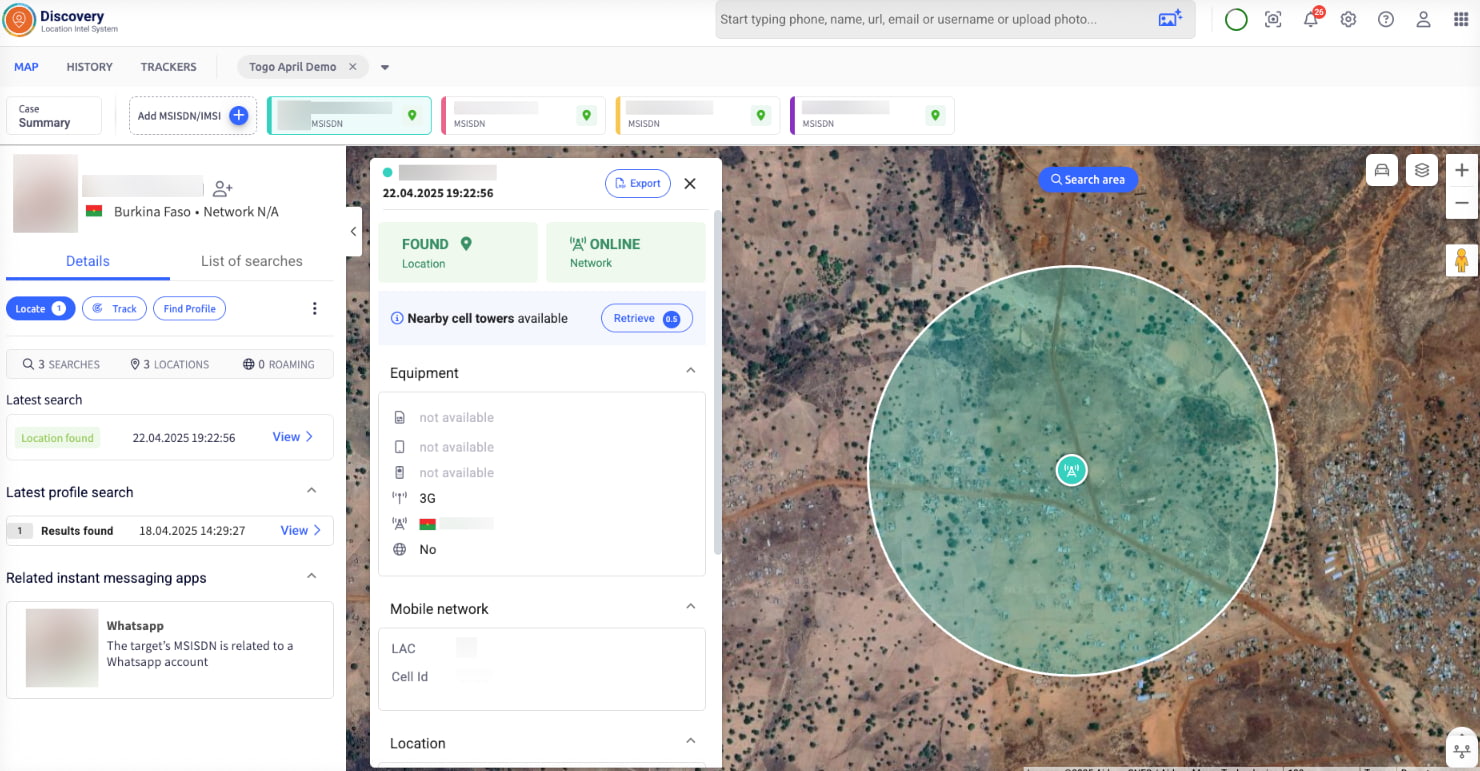
I dropped in the three numbers to see their location. These could’ve been burner phones. But if they were still online, Discovery would find them.
Within seconds, two devices returned results. One showed up just outside Kandia. The other – near Koundjoaré.
And the timing matched the intel. Right where and when we were told they’d move. I’ve set a geofence and started monitoring their movement. If those numbers entered the Koundjoaré area and if the third number was turned on, Discovery would alert me.
Step 2 — Reconstruct the movement
Once I confirmed they were active, I needed to understand their past behaviour. Did their route match the paths already known to us?
Criminals often swap SIM cards, but the phone stays the same. That’s where ad data becomes useful. Quadrant pulls historical location from anonymous smart devices. Traces left by everyday apps. I collected the smart devices from the area where the phones were active in Discovery. If the model of the phone matches the info from Discovery, we might have confirmation and can link the same actor across time.
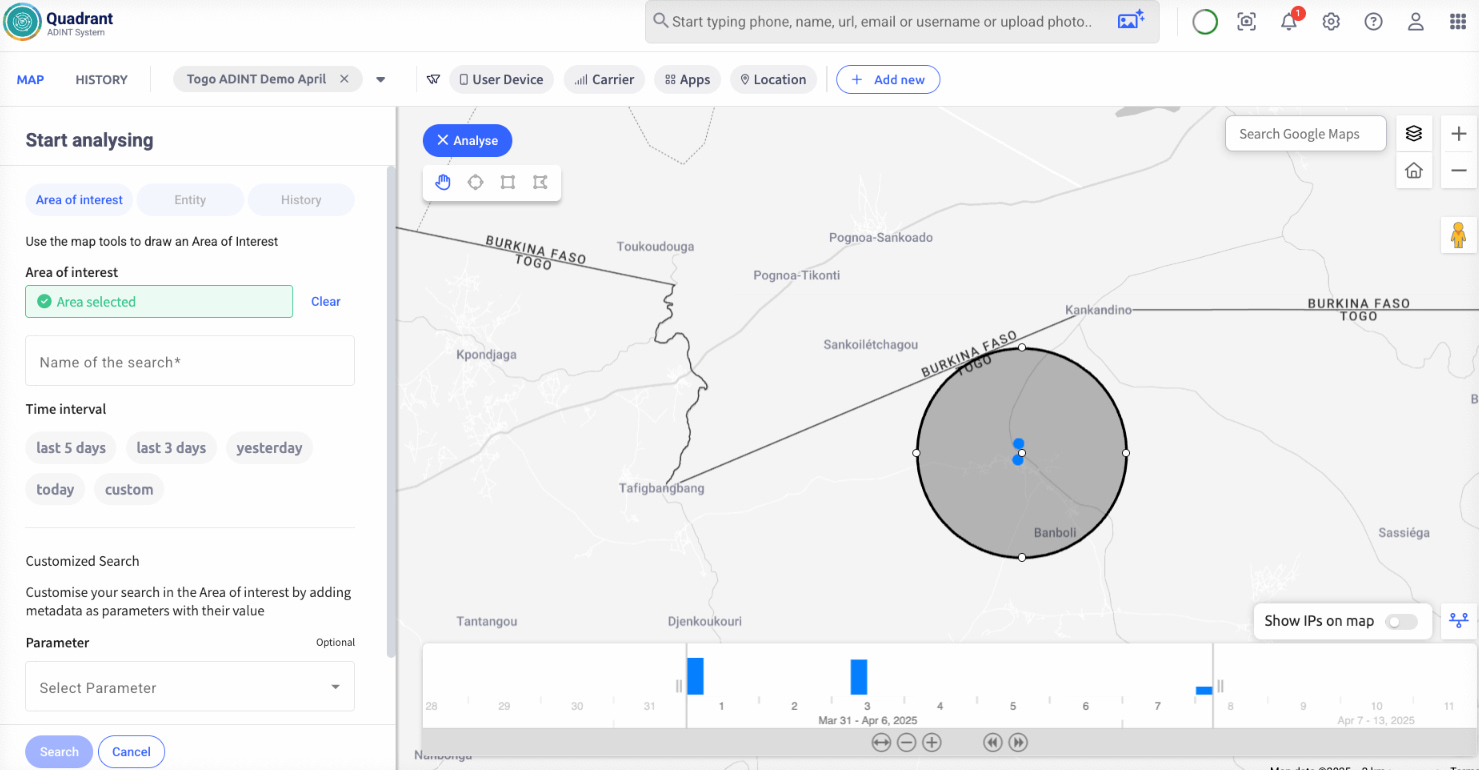
I tracked their current route with Discovery to get several locations. Then I used Quadrant to pull two weeks of those devices’ behaviour across the northern corridor.
The pattern was clear.
Similar stops. Similar pauses. Repeated signals near a known logistics house outside Kandia. And both had passed the Koundjoaré outpost.
We correlated the Ad-IDs with the phone numbers based on their similar movement patterns. This confirmed that the same individuals had followed a known route. It showed that the info from Discovery and the historical traces from Quadrant were coming from the same devices. That gave us the operational confidence that we were tracking the right targets.
Step 3 — Confirm coordination
Then came the third number.
It had been silent during our initial sweep. But a day later, it lit up near a different crossing point. We got a notification from Discovery, the phone had been turned on. Then repeated the same process with Quadrant. Similar path. Same pauses. Same recruitment trail.
But offset by 72 hours. They weren’t travelling together. They were taking the same route, just offset in time. That’s a common tactic to avoid detection.
Step 4 — Identify the organiser
If this were a real operation, they would have done their homework.
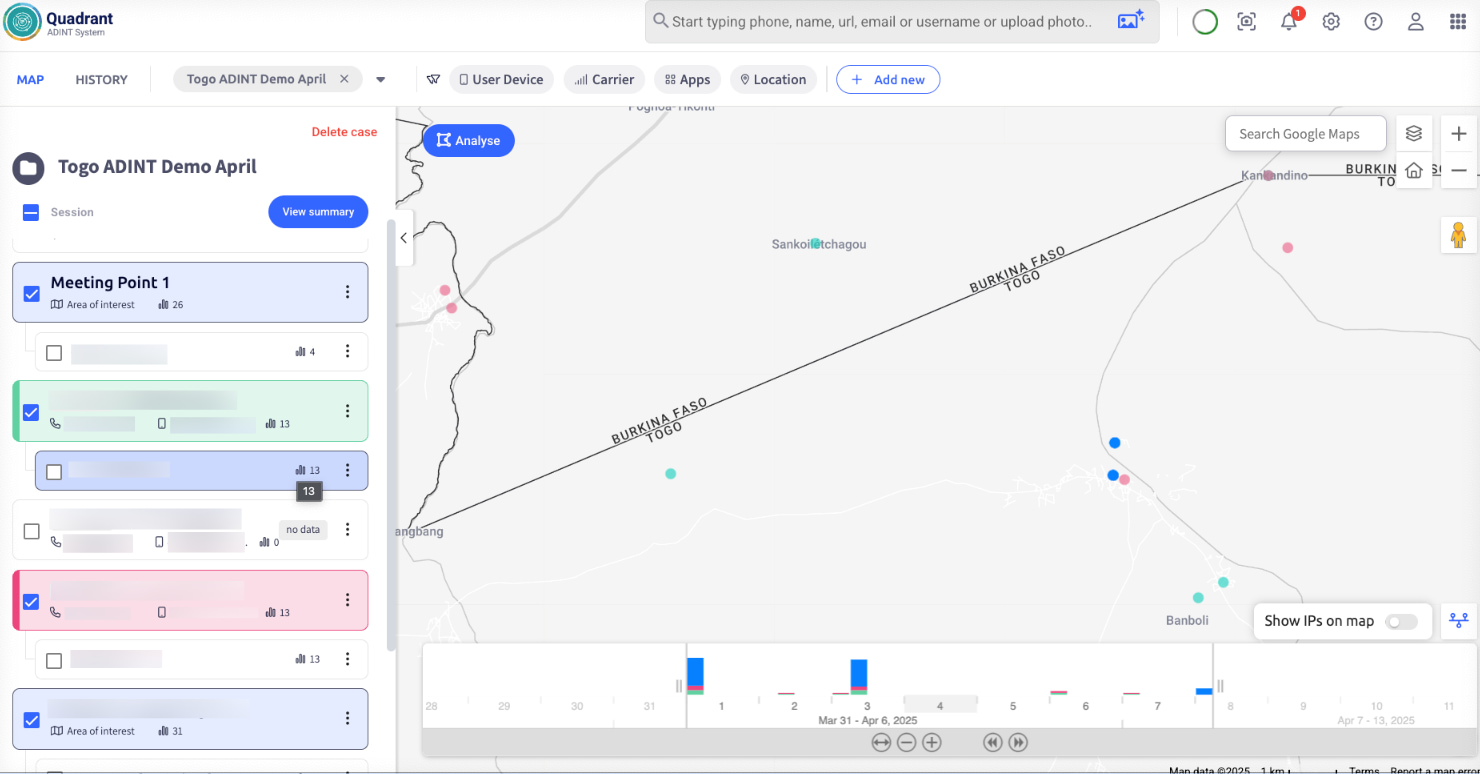
I kept using Discovery to monitor the numbers’ movement around the gendarmerie outpost. They followed the same path, made short visits, and always in the same time window.
That’s reconnaissance.
Quadrant confirmed the overlap. All three devices had paused near the outpost multiple times.
I analysed the area.
And noticed another signal.
A fourth ad ID. Same route. Same timing. Minimal app use.
That was the organiser.
Step 5 — The site
I let Discovery build a full movement timeline. Quadrant showed me a clear pattern.
Both systems confirmed the same location.
A house south of Koumongou. No traffic. No utilities. No reason to be there. But all four ad profiles visited it. Multiple times. Always after sunset.
This wasn’t a shelter. This was a site.
Insights from both systems confirmed repeat meetings. Each suspect stayed within a tight timeframe. Same devices. Similar app patterns and behaviour.
This was a planning space.
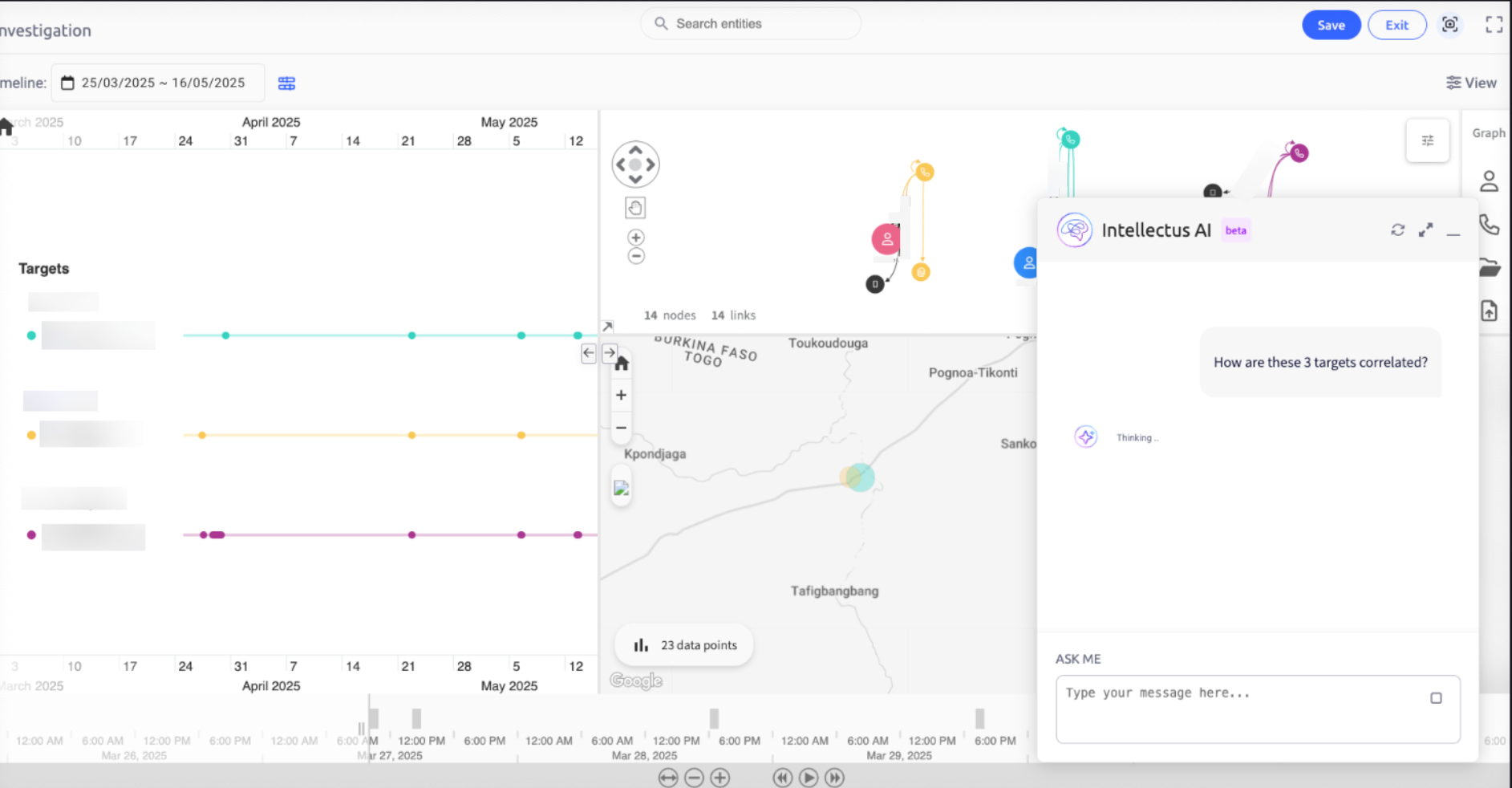
Step 6 — The network
I focused on the fourth device.
Quadrant’s digital profiling showed me banking app activity. And patterns from other app usage.
I used cross-analysis to identify similar behavioural profiles. Three more emerged. All tied to short bursts of movement near the outpost and the house.
It wasn’t four suspects anymore. This was a network expansion.
Outcome
Quadrant showed me patterns. Discovery showed me movement. Together, they mapped the structure.
I built operational timelines. Layered them with activity windows.
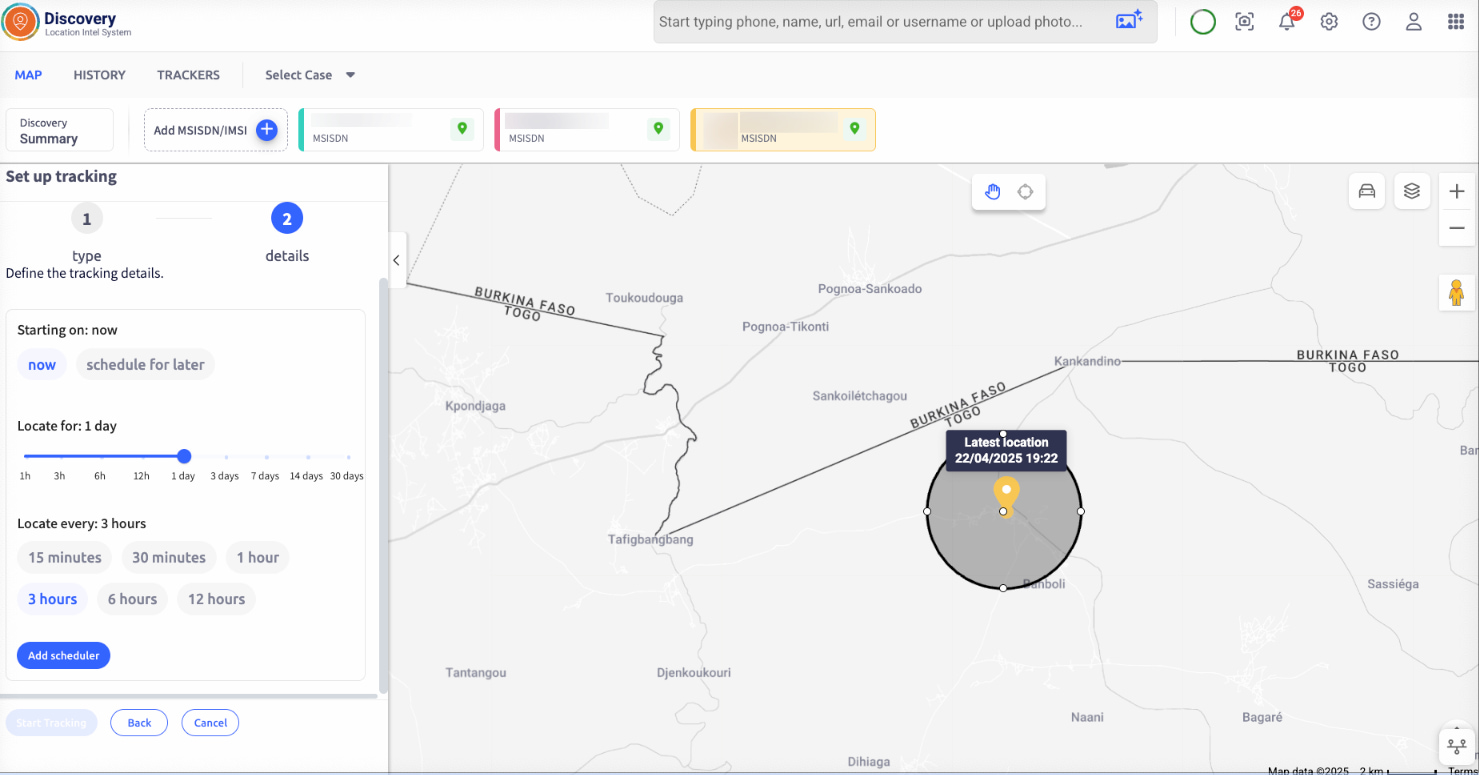
I set up geofences with Discovery’s smart alert tool. One around the gendarmerie. One around the safe house. One at the entry trail near Tandjouaré.
Now, if any of them move, I’ll know before they get close. Even if the numbers change, the behaviour gives them away.
This time, we’re not reacting.
We’re ahead of it.
This is what Securing Better Lives looks like.
Book a demo
Experience how Intellectus helps agencies solve cases faster, with a live demo from our team.
