Brief
Poaching isn’t just about hunters. It is a supply chain with scouts tracking patrols, strike teams moving in at night, couriers crossing borders, and organisers arranging buyers overseas. By the time a rhino is killed, the horn can be on its way to another country within hours.
This use case shows how Intellectus AI Ecosystem could help expose and disrupt a cross-border network. With no witnesses and little time to act, investigators can rely on open-source intelligence, ad intelligence, and real-time geospatial monitoring to uncover the network before the next kill.

You are the investigator on this case. It is late at night, patrols are stretched thin, and you’ve just received a tip that a team may be moving tonight. You don’t know if the tip is valid, but another rhino could be gone by dawn. In many poaching investigations, rangers already know the names of the hunters on the ground, but the real challenge is uncovering the organisers, fixers, and buyers behind them. With almost no physical evidence to work from, your only chance is to follow the digital traces this network leaves behind. Where do you begin, and how do you follow the trail before it is too late?
Step 1: Compass
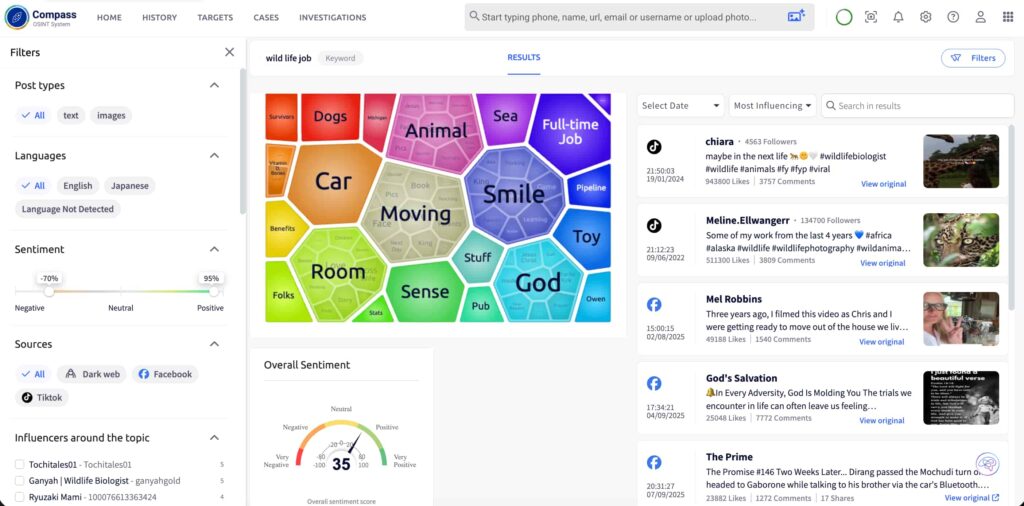
Begin by running keyword research in Compass, scanning for chatter around illegal hunting. Many posts point away from legitimate activities and into closed spaces where coordination happens. One thread in a local group stands out: coded references to “night walks” and “special deliveries.” Too vague, too familiar, you think to yourself as you read the post. Compass pulls these fragments together and links them back to social media profiles. From there, you uncover the profile behind the posts and begin building a digital profile of your person of interest. You can see it’s linked to an instant messaging account which gives you a phone number to work with.
Step 2: Discovery
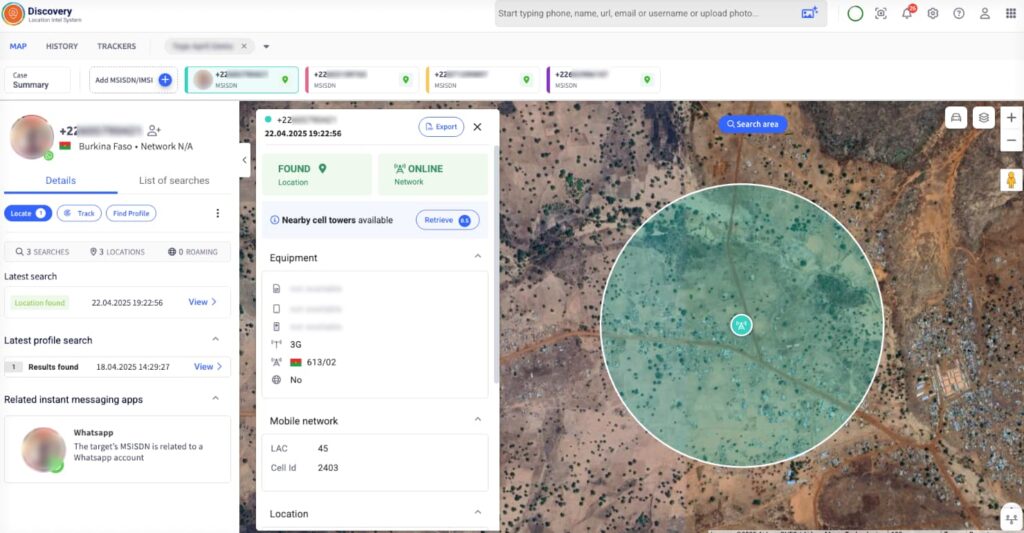
Now that you have the number, pivot to Discovery. Check first that it’s active and not just a burner phone. Once confirmed it’s active, set a tracker on the device. From this moment on you can monitor his movements. If those numbers enter the national park area, Discovery will alert you.
Step 3: Quadrant
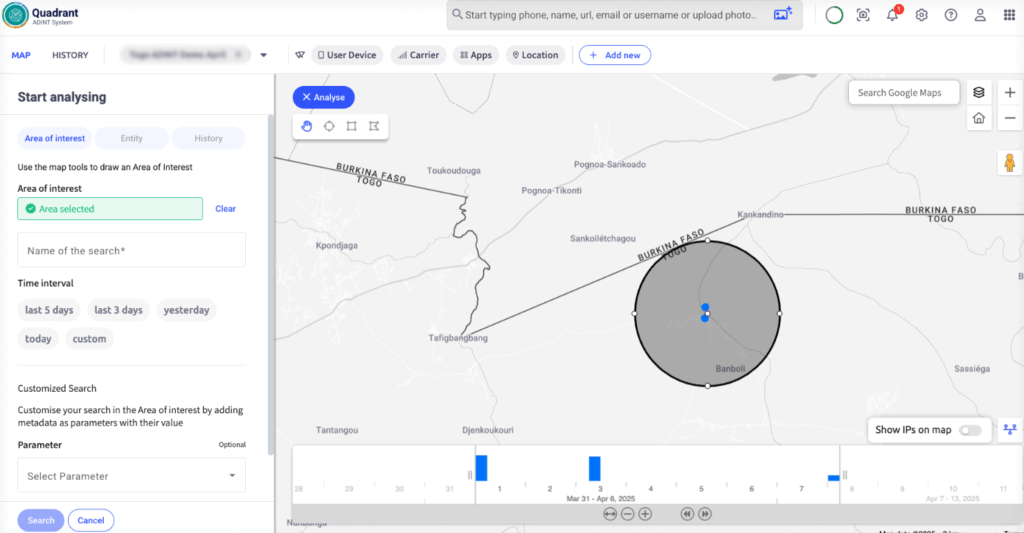
With the number confirmed active and monitored, shift to Quadrant. You need to understand past behaviour. Criminals may swap SIM cards, but the phone stays the same. That’s where Quadrant helps. It analyses historical advertisement data. You analyse known poaching spots and collect Ad IDs present. You already have the current movements of your POI from Discovery, so now you can use Quadrant to cross-reference the data, confirm the suspects’ Ad ID, and build a behavioural timeline covering weeks of his movement.
The pattern is clear: similar stops, repeated pauses, and overlap with known safehouses. Here you notice other Ad IDs also present. You suspect these could be scouts and couriers, moving alongside the organiser’s device. Now you can start mapping the poaching network.
Step 4: Pulse
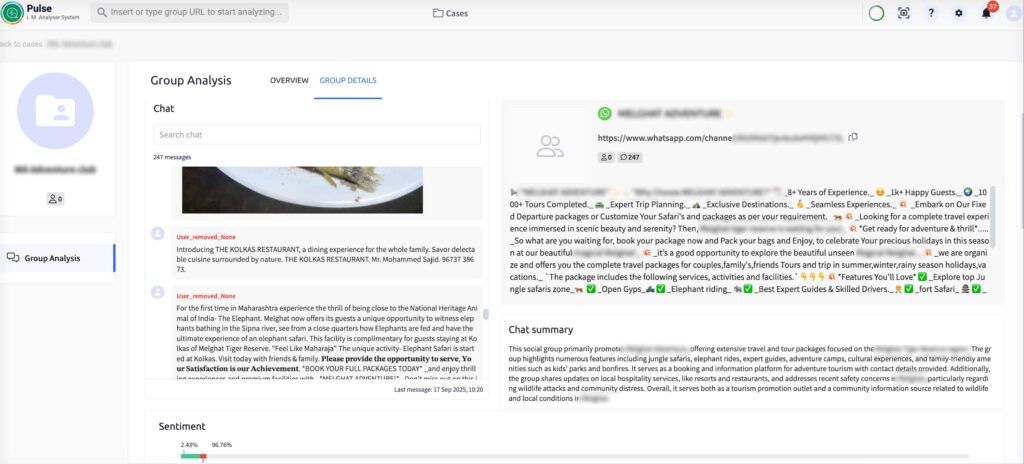
You’re deep into analysis when a colleague suddenly interrupts, dropping new intel on your desk: they have uncovered a WhatsApp group believed to be run by the poaching network. Use the Pulse System to analyse this group. Read through chat summaries, sentiment, and top keywords to map out the tone of the group and identify key figures. From the conversations you can see when and where they are planning their next poaching attempt. You prepare the intelligence package and send it to the tactical team, giving them the chance to intercept before the strike can happen.
Step 5: Act on the intelligence

Armed with the insights from Pulse, Discovery, and Quadrant, you hand over a clear picture to the tactical team. The data shows who is involved, where they plan to strike, and when. Rangers move into position quietly, intercepting the group before they can reach the rhino.
Outcome
From a single lead, we exposed the organiser, identified his team, and disrupted the route. Most poaching cases end with a carcass on the ground. This one ended with prevention.
This is what Securing Better Lives looks like.

